[UPDATE: August 10, 2014]
Some good news for those affected by CryptoLocker!
FireEye and Fox-It (two companies that provide corporate security solutions) have created a support web site called DeCryptCryptolocker (www.decryptcryptolocker.com).
Those who are infected with CryptoLocker can go to the DeCryptCryptolocker site, which allows you to enter your email address and then upload to them one of your infected files. You are then sent an email message that includes the code necessary to decrypt the file, and a link to special recovery software that helps you decrypt all the infected files.
Continue on to read all about CryptoLocker (and other ransomware) in the original article…
I hear about new viruses almost every day, most of which your anti-virus program protects you from. But this particular virus (or malware) is a bit different, which is why I want to devote some time to it here.
What is “malware”?
Firsts of all, let me explain the terminology I just used. “Malware” comes from the words “MALiscious softWARE” and is really just a generic term that encompasses any intrusive computer program or script that disrupts the operation of your computer.
Examples of malware include computer viruses, worms, trojan horses, keyloggers, ransomware, spyware, adware, and malicious browser-helper-objects (BHO’s), just to name a few.
Does that make sense?So when talking about a computer virus, for example, I can call it a virus, or I can call it malware. The bottom line is, it’s a bad thing for your computer.

What is CryptoLocker?
Now, back to the topic at hand. CryptoLocker (which is sometimes spelled as two words “Crypto Locker”) is a malware program that’s been making the rounds the past month, and is an example of a type of malware called “ransomware“.
Ransomware is not a new thing, but this particular instance has been more widespread and damaging that most.
Here’s how CryptoLocker (and most ransomware) works.
Note that I got a lot of this information from a well known security company called Sophos (www.sophos.com) that had some great articles on CryptoLocker. I have links to them at the end of this discussion.
- You get what seems to be a legitimate email with an attachment from some company like UPS or FedEx sending you a tracking notification, but instead it’s phishing email (i.e. it looks like it’s legitimate but it’s bogus).
- You open the email and then click an attachment to open it, and you’re instantly infected with CyrptoLocker.
- The malware installs itself into your Documents folder and sets itself up to automatically start every time you start-up Windows by putting itself into the Windows registry.
- It then uses your internet connection and attempts to connect to one of dozens of servers on the Internet that have been specifically setup by the bad guys.
- Once it connects to a server, CryptoLocker uploads to that server a public-encryption key. Using that key, the server generates a private-public key pair, and sends the public key to your computer, keeping the private key.
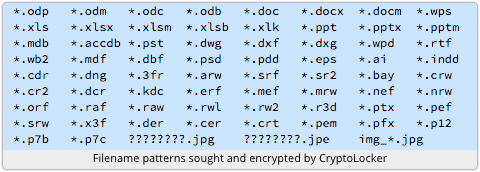
- CryptoLocker then scans your hard drive and any other attached storage device (such as a portable hard drive or flash drive) for certain types of files, including documents and pictures.Here is a screenshot from Sophos that shows the file types CryptoLocker goes after…
- Each file it finds is encrypted using the public key. This means you can no longer open the file (it’s incrypted) unless you have the private key (which you don’t).
- CryptoLocker then displays a ransom page telling you that you have 72 hours to pay (usually $300) for the private key which will let you unencrypt your files.Here is another screenshot from Sophos showing you what the ransom page looks like…
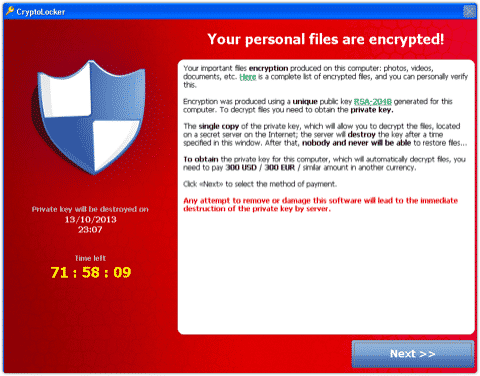
- If you do NOT pay, the private key is destroyed by the server that it’s on, and you have no way to unencrypt and use your files.
- If you DO pay, it’s been reported that the bad guys DO actually provide you with the private key so you can get your files back.
Sounds like something out of a movie, doesn’t it? The truth is, that it’s almost impossible to unencrypt your files, and many people have been known to pay the ransom to get back their precious files.
Sophos put together a nice YouTube video that shows you CryptoLocker in action. It’s really kind of fascinating to watch…
Click the video below to play…
The two buttons at the lower right
let you go FULL SCREEN or CHANGE QUALITY —>>>
So how do you protect yourself?
 I’ve written a lot of other articles about staying safe on the Internet…. and in fact, have a book called Staying Safe on the Internet that you can CLICK HERE to read more about.
I’ve written a lot of other articles about staying safe on the Internet…. and in fact, have a book called Staying Safe on the Internet that you can CLICK HERE to read more about.
- Make sure your Anti-virus program is up to date and that the virus definitions are getting updated.
- Make sure your Windows updates are happening, since they often contain security fixes.
- Make sure common programs you use on the Internet (Adobe Flash Player, Adobe Reader, Java) are updated. And frankly, as I’ve mentioned in other articles, just completely uninstall Java if you aren’t using it.
- Avoid opening any email attachment you weren’t expecting.
- Don’t fall for any phishing emails (i.e. emails that look like they are from legitimate companies asking you to open an attachment)
- Make regular backups that you store away from your computer.
 Here are some links to more information…
Here are some links to more information…
I’ve written a lot of articles about staying safe on the Internet. If you’d like to see them, here’s a link to the “master list”:
Sophos has two good articles that give you more details about CryptoLocker:
As always, I’d love to hear about your own personal experiences with Internet safety and if you know of anyone who’s had an encounter with CryptoLocker
Please Stay Safe!!!






Great article. 12/31/12 I was hit with such a virus. They wanted $300, I was to go to Walgreen or Walmart. Get one of their money cards and put some code on this website that would not go away. Instead I went to Office Max, they got the virus off my pc, I updated Norton to Norton 360 and it cost me about $240. I don’t know how I got the darn thing, I was on the web looking for a quilting store in Grand Island. Oh I guess, things happen.
Hi Pamela…
Wow… so you had a case similar to what we talked about here! Glad you eventually got things taken care of, but so sorry you had to spend the money!!!
Cases like this are when you really start having bad, bad feelings toward the “people” (Ok, how about I say “idiots” instead) who write these viruses and malware programs. You just want to scream, “get a life”.
Anyway, thanks for sharing the story. Hopefully your Norton 360 (which I also use) will keep the bad stuff off from now on!
Take care…
John Lortz
Excellent article. Thanks for the update on possible intrusions by unwanted malware. I am in the processing of backing up both of our computers this afternoon. I am as summing that CryptoLocker has no affect on Apple products.
Thanks Again!
Hi Wayne!!! Great to hear from you!
Yes you are correct that CyrptoLocker is only a Windows issue (at this point). As you know (but perhaps others reading this won’t) viruses and malware have to be created for specific operating systems (like Windows), which is why you don’t see quite as many for the Mac. The Mac OS is a smaller target for hackers compared to Windows, so they tend to leave it alone as being “not worth it”. That’s a good thing for Mac users!
Hope all is well with you and Nancy!!!
Take care
John Lortz
What will happen to Vista (which I have now). Thanks
Hi Marty…
Windows Vista is not affected by the “end of life” issue for XP. At this point, Microsoft is slated to continue updates for Vista until April 11, 2017, so you still have plenty of time to use your Vista computer with no worries.
Thanks for leaving the message! Take care…
John Lortz
So insane to think about how technology evolves, so do crimes… It’s so important to have the professionals handle these situations.
Thanks for the post